October 19, 2021
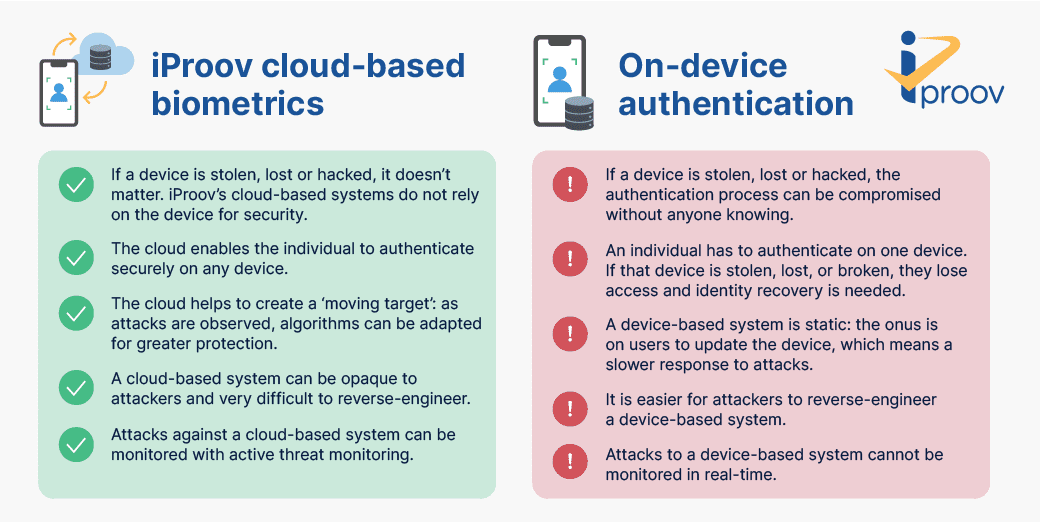
A key question for anyone evaluating biometric technologies is: should the authentication take place on-device or in the cloud?
At iProov, we believe that cloud-based, or server-side, biometric authentication is a great option for securely authenticate users remotely. We use the cloud because:
- Devices are vulnerable. They can be stolen, hacked, lost, or damaged. If the authentication is taking place on the device, then any organization using biometric authentication has to trust the integrity of the device being used. At iProov we take a secure approach by assuming that neither the user nor the device can be trusted.
- The cloud enables active threat monitoring. iProov is able to monitor and analyze attacks on our systems in real-time because we use the cloud. Our iProov Security Operations Center (iSOC) observes attack techniques and applies machine learning to help us adapt quickly to novel threats, which increases the security and protection that we can provide to our customers and their users.
In this article, we’ll discuss the advantages and applications of cloud-based versus on-device authentication.
Cloud vs on-device biometrics: what’s the difference?
Scenario 1, cloud-based biometrics: You need to send a large sum of money to a friend. You access your bank via your mobile device or computer. First, your bank needs to double-check that you are the genuine account holder so it can authorize the transaction. To do this, it prompts you to iProov with Dynamic Liveness. You present your face to the user-facing camera and a short sequence of lights illuminate your face. The imagery and unique sequence of lights is sent to the server to be analyzed and verified against the image you provided at onboarding. This ensures you are the right person, a real person, and are authenticating right now.
The entire authentication process happens server-side, independently from the device. This means that a device affected by malware, for example, will not compromise the authentication process.
Scenario 2, device-based biometrics: You begin the process of transferring money via your mobile device. Again, your bank needs to confirm that you are who you say you are, so you authenticate using biometrics (such as by presenting your face to the camera or fingerprint to a sensor). Only this time, the entire authentication process takes place on the device, which means it is dependent on the device being secure. If the device has been stolen or hacked, the bank or other organization would not be able to detect this and the transaction could potentially be fraudulent.
So, the former processes the authentication on a cloud server, while the latter processes the authentication locally. The main difference is the additional security that cloud-based authentication can deliver over device-based authentication, but there are also many other advantages to using the cloud.
Cloud based authentication, verification, and identity recovery
Before we move on to look at the advantages of cloud in more depth, let’s consider when organizations use biometrics for online identity verification and how the cloud is used in each one:
- Identity verification for onboarding: When you use iProov to onboard an online customer, the process will likely involve the verification of the user’s physical face against the image in a trusted document, such as a passport or driver’s license. This process needs to be completed in the cloud.
- Authentication: Once the user has onboarded, they can use iProov to authenticate themselves on an ongoing basis. Apple Face ID and other on-device authentication can work for low-risk scenarios, but if a customer wishes to transfer money or complete other secure processes, a cloud-based authentication is needed to ensure it is the legitimate user and that the device has not been compromised.
- Identity recovery: If a user loses their device, or it breaks or gets stolen, they lose the ability to authenticate themselves. Cloud-based identity verification is necessary to enable users to securely access their apps and services via another device without needing to re-enroll. There’s no need for any lengthy identity recovery process because the credentials are stored in the cloud rather than a device.
Cloud-based verification forms an essential part of the online customer lifecycle – critical for onboarding, authentication, and identity recovery.
The benefits and advantages of cloud-based biometric authentication
1: Security
Why is cloud-based biometric authentication more secure than on-device?
- Cloud-based biometric authentication is unaffected by vulnerabilities on the device (or execution environment). The biometric process is hardware-independent, and the device is simply the medium or facilitator. The security is in the cloud, not on the device.
- Biometric authentication software operating in the cloud is opaque to an attacker and can be more difficult to reverse-engineer than on-device authentication.
- With on-device authentication, the onus is on the device owner to keep their device updated with the latest device software and security patches. This means that it can take longer for organizations and system providers to address new threats, which creates vulnerabilities. With iProov, algorithm updates can be made within the cloud to ensure defenses against new and evolving threats are updated rapidly.
- If you are using iProov’s Dynamic Liveness, you also benefit from active threat monitoring. This is an iProov-specific advantage, where the iSOC provides you with continuous security against new threats. Response to new and evolving attacks can be much faster and more efficient in the cloud. Defenses and algorithms can be updated continually in response to new threats, which makes life much harder for attackers, as the cloud-based processes are a moving target. This ultimately means that we learn more about the attackers than they learn about us.
On-device authentication can be trusted if — and only if — the integrity and identity of the device and its user can be trusted. If a device is compromised through malware or a digitally injected attack, then the user’s biometric data could be extracted or spoofed.
This means that, for an organization, each device is a source of risk, which is a potential insecurity.
The bottom line is: with cloud-based biometrics, organizations can protect themselves against the risk of fraudulent authentications taking place on compromised devices. This is a huge advantage as cybersecurity threats evolve.
2: Privacy
The privacy of data depends on the company collecting it and the operational environment.
For instance, at iProov we use a privacy firewall and strong encryption techniques to protect highly sensitive data to safeguard the user’s confidentiality. The biometric imagery is stored as an encrypted biometric template, which is referred to using an anonymous pseudonym. This is not associated with anything that could reveal the users’ identity.
Ultimately, privacy of data comes down to how it is used, the company using it, and the laws and regulations they adhere to. Cloud-based identity verification providers, such as iProov, are regularly audited and comply with ISO 27001 and 27701 certifications, validating the security and privacy capabilities of the cloud for managing data securely.
3: Hardware: extend to other devices
It’s easier for cloud-based applications to be deployed across a wide range of platforms and hardware. iProov technology in particular can be deployed on any device with a user-facing camera, including:
- Mobile devices, such as iOS and Android
- Computers and laptops
- Tablets
- Kiosks
- Web browsers
Once the user is ‘iProoved’ with a particular organization, they’re immediately able to access the service or account on any device.
With an on-device solution, a user would lose access to that organization’s online services if the device they had verified on was lost, stolen, or damaged. Identity recovery would be necessary to get them up and running again. This is because the device ID will be linked to a user’s ‘profile’, and if the device ID changes they would need to re-onboard and reverify. However, with iProov, once you’ve verified you can simply authenticate on any device, even if the original device was lost, broken or stolen.
4: Inclusivity
The cloud can also enable organizations to reach the widest possible audience online. With iProov, you can ensure that users have access to your digital services even if they don’t have access to a smartphone, computer, or tablet.
iProov’s cloud-based technology can be extended to kiosks to ensure that people are not excluded from securely accessing services. These kiosks can either be offered unsupervised in shopping malls or travel hubs, or situated in banks or government offices where staff can be on-hand to offer support.
And across all of these devices, iProov ensures a consistent user interface — designed to combat selfie anxiety — to reassure customers.
5: Convenience and user experience
iProov’s cloud-based technology also makes identity recovery simple. Data shows that people replace their phones around every three years, which means many people need to recover their identity on services or apps every year. This poses two main problems:
- Inconvenience for the user (often involving a tedious recovery process) which could increase churn rates and cause frustration for users
- Security risk if the phone is sold without being wiped or is stolen
Because iProov authentication occurs on the cloud and not on the device, recovering identity on a new or replacement device is simple. iProov creates trust in the person holding the device rather than the device itself. All that’s needed is a brief Dynamic Liveness face verification on each device, rather than resubmitting all of your documentation or needing to speak to a customer service representative to prove your identity.
This also means that, if required, user journeys can be started on one channel and completed in another.
Here’s what it looks like in practice: A bank’s customer is travelling abroad and loses their mobile phone and credit cards. To access cash and arrange for replacement cards, they use a friend’s device. They authenticate themselves in the same way they would have done on their own device — an effortless biometric face scan processed on the cloud. This simple process enables the user to access the required services with a recognisable, reassuring customer experience. No biometric information is left on the shared device, reducing risk and protecting privacy.
Cloud biometrics vs on-device biometrics: a summary
- Cloud-based biometrics are necessary throughout the online customer lifecycle; for onboarding, identity recovery and for any authentication that is not low-risk.
- On-device authentication is useful for every-day activities, such as the unlocking of personal devices, where the threat is low.
- Cloud authentication is needed for activities where there is a risk that fraud or other crime could be committed if a device has been compromised.
- iProov’s cloud-based service can offer greater security than on-device systems. On-device authentication can be trusted if — and only if — the integrity and identity of the device and its user can be trusted. iProov assumes the user and the device have been compromised.
- iProov also provides active-threat monitoring, which is made possible by the cloud, through the iProov Security Operations Center (iSOC) to quickly respond to evolving attack types.
- It’s easier for cloud-based applications to be hardware-agnostic. iProov works across mobile devices, tablets, computers, and kiosks.
- The cloud enables greater inclusivity to reach the widest possible audience. iProov can be extended to kiosks to ensure that people are not excluded from securely accessing digital services if they do not have access to a smartphone or other device with a user-facing camera.
- The cloud offers greater convenience to the end-user, for example making the user experience for identity recovery much easier.
This is why iProov is trusted by some of the world’s most demanding organizations — such as the US Department of Homeland Security, the UK Home Office, Knab, and Rabobank — to provide secure online user verification and authentication.
If you’d like to know more about how our cloud-based biometric technology can help your organization to verify and authenticate users, click here to book a demo.