November 14, 2023
iProov and Ping Identity share the common goal of establishing trust in digital interactions. The need for strong authentication and verification methods has never been more crucial as organizations seek to ensure that their online users are authentic.
Passwords and secret questions were once adequate. Today, 74% of all breaches include the human element – with people being involved either via error, privilege misuse, use of stolen credentials, or social engineering. Authentication and verification technology has advanced considerably as the need for more robust measures has grown. Now, it’s essential to bind digital identities to real-world government IDs rather than just something a user knows.
However, cybercriminals are also keeping pace, and Generative Artificial Intelligence (Gen AI) has accelerated the development of cyberattacks and fraud. AI is neither good nor evil – it’s a tool that’s employed by both cybersecurity organizations and threat actors alike. One thing is certain, though: it poses a significant challenge to organizations seeking to protect their users and data.
iProov and Ping have integrated their best-in-class technologies to utilize face biometrics as part of identity verification and a wider Identity and Access Management (IAM) solution to defend against cyberattacks, credential compromise, and fraud at scale. Read on to discover how Ping and iProov’s groundbreaking technology works and why we have partnered to combat the growing threat of Generative AI.
What is Generative AI, And Why Is It A Problem?
Generative AI utilizes algorithms to generate fresh content in the form of text, images, videos, or other media in response to given inputs or prompts. Gen AI generally leverages AI technologies such as computer vision and neural networks – these enable computers to derive information from images, videos, and other visual inputs to make actions or decisions based on what they “see” based on that information. These technologies have given rise to the increasing use and quality of deepfakes and other synthetic imagery.
Gen AI poses a threat to online identity assurance. The ultimate aim of identity verification is to establish that the user is who they claim to be remotely. But with Gen AI, it has become increasingly easier for fraudsters to impersonate others or render new identities from scratch by utilizing tools like ChatGPT (and its evil twins Fraud & Worm-GPT), and other tools to create voice clones and synthetic imagery.
Gen AI is no longer a technology of the future. In fact, research shows that humans can “no longer meaningfully distinguish between AI-generated and human-created digital content,” and easy access to the aforementioned tools means that low-skilled threat actors can launch targeted attacks with relative ease.
Choosing the right user verification and authentication solution is now critical. iProov and Ping have developed solutions to address this problem, with an approach aimed at simplifying online user verification while maintaining the highest level of security. Organizations must embrace advanced techniques that adapt to the rapidly accelerating landscape of cyber threats, utilizing AI for the good of cybersecurity.
How Does iProov and Ping’s Joint Solution Work to Combat Generative AI?
The use of AI can also enhance accuracy, security, and speed in identity verification processes. Deep learning models, including Convolutional Neural Networks (CNNs), can help detect and match images. At the same time, computer vision can help ensure that the imagery belongs to a real person and not a deepfake, mask, or other synthetic media.
With the implementation of a robust facial biometric verification system, organizations can easily mitigate most of the threats posed by Gen AI. By scanning their faces with a passive challenge-response mechanism and adding a trusted identity document such as a passport or driver’s license, users can remotely opt-in to verify their identities with utmost security.
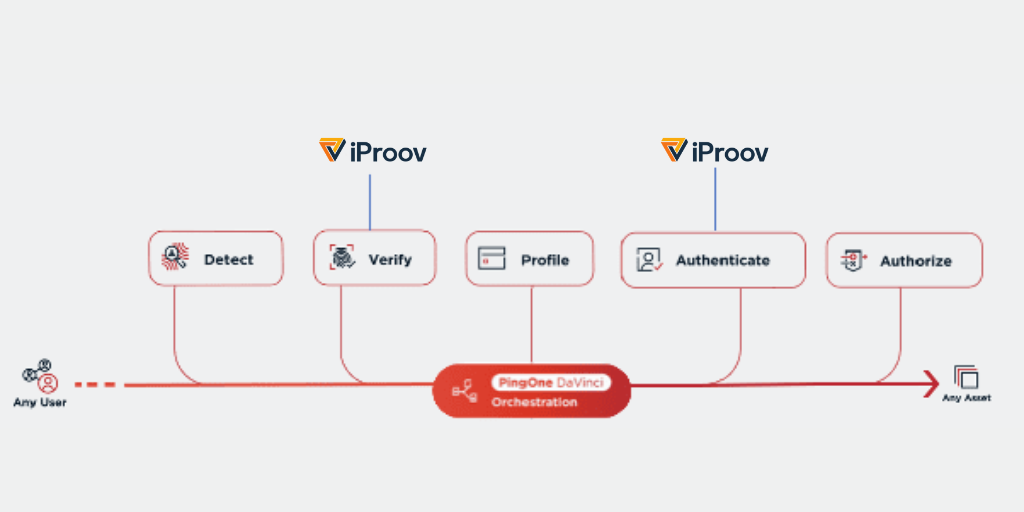
In this context, iProov and Ping’s technologies stand out as market leaders. Let’s consider how iProov and Ping’s technologies work in more detail:
Ping: Identity Security for the Digital Enterprise
Ping allows organizations to design, test, and optimize digital identity experiences with PingOne DaVinci for easy creation of frictionless security.
Ping’s open architecture enables customizable identity architecture where decentralized digital identity applications like PingOne Neo put users in control of their identity, effectively protecting against data breaches and other security incidents. Ping takes a multi-faceted and customizable approach to threat protection, with a proven track record of detecting bots and account takeovers even before the session begins.
Decentralized identity helps defend against AI-based attacks by limiting the incentive for the attacker and reducing the risk of a compromise. With DCI, the attractiveness of a hack is massively reduced as a breach likely results in a single individual’s records being compromised–as opposed to the sensitive data of millions of people in a centralized system. DCI also makes it harder for cybercriminals to successfully execute takeovers and fraud with digital credentials, which provide a secure and tamper-proof way for people to authenticate themselves.
PingOne Neo is the only solution on the market that offers native digital credential issuance and verification. Neo is architected to limit how much identity information is collected and stored by organizations. This approach is critical to preventing data breaches and security incidents. Learn more about Identity Solutions in the Age of AI here.
Discover more about Ping’s products and their capabilities below:
iProov: Mission-Critical Biometric Face Verification
iProov’s patented biometric solutions suite assures that an online user is the right person not an impostor), the real person (not a spoof), and is authenticating right now (using a one-time biometric).
iProov’s science-based face biometric verification uses computer vision technology to detect the genuine presence of a living user with a time-limited session code that illuminates the face with an unpredictable sequence of colors. Deep-learning techniques then analyze the reflected sequence to confirm real-time authenticity, analyzing multidimensional information derived from facial behavior and other contextual data for comprehensive identity assurance and identity fraud risk mitigation. Traditional timestamp methods which can be falsified are not adequate to ensure real-time authenticity.
To confidently detect that an individual is a ‘live’ person, technology leveraging artificial intelligence is needed to ensure they are verifying in real-time. This is the only way to effectively mitigate digital injection and Gen AI attacks with the highest level of assurance. iProov also incorporates active threat monitoring and response enabling us to respond to zero-day vulnerabilities and stay one step ahead of Gen AI attacks.
In the fight against Gen AI, organizations must bind individual’s digital identity to their real-world, government-issued ID and ensure they do so in real time. This identity should be reusable so individuals can authenticate with the same credentials throughout their user lifecycle. iProov and Ping make this process simpler and more secure than ever before, offering the versatility to apply the appropriate authentication technology for each transaction according to the risk of the activity, with Flexible assurance levels in the iProov Biometric Solutions Suite – LA (Standard) and GPA (Premium) – available in one integration
Advantages of Employing iProov and Ping’s Joint Solution
You can deploy iProov and Ping for a range of use cases, including using face biometric verification for passwordless login, multi-factor authentication (MFA), account recovery, and step-up authentication. It’s ideal for organizations looking to bolster their cybersecurity posture while delivering a frictionless customer experience.
The two solutions complement each other, combining Ping’s industry-leading IAM/CIAM and iProov’s biometric verification with best-in-class liveness detection to offer a powerful, end-to-end solution. Advantages of this include, but are not limited to:
- Enhanced Regulatory Compliance: Secure digital onboarding and authentication support regulatory compliance – certified under eIDAS, complying with KYC, AML, Strong Customer Authentication (SCA), and GDPR – safeguarding customers against fraudulent attacks while utilizing digital channels.
- Improved Security: Ping’s adaptive authentication and customizable security measures, coupled with iProov’s award-winning biometric security – all monitored by the iProov Security Operations Center – drastically minimize the risk of various fraud types. This may include account takeover and synthetic or stolen identity fraud, as well as data breaches – which can be costly for organizations and damaging to their reputation.
- Ease of Integration: Both iProov and Ping are cloud-delivered solutions equipped with lightweight, cutting-edge SDKs. These enterprise-proven technologies are easily integrated with any API, web, mobile, or SaaS application, regardless of its location, using various APIs, SDKs, and SSO integrations. Ping’s DaVinci orchestration engine can be used to integrate with hundreds of other business applications.
- Improved Conversion rates: iProov in production success rates typically >98%.
- Enhanced Customer Experience: The experience surpasses past online security methods by being exceptionally fast and frictionless. The solution is independent of platform, format, or device.
For more information on Ping and iProov, check out our integration listing. Alternatively, book a demo of iProov’s solution here or begin a Ping free trial here.
