December 12, 2019
You’ve probably heard the term ‘Liveness’ used within the authentication market. But have you heard of ‘Genuine Presence’? At iProov we use the term genuine presence a lot (and not just because we coined it.) It’s printed on our leaflets, our swag… we’ve even had #genuinepresence printed on t-shirts.
Why does Genuine Presence matter?
Determining Genuine Presence is critical to safeguard digital identity. Without Genuine Presence Assurance, mass fraudulent authentication claims can and will be passed. Undetectable attacks will be scaled and digital identity compromised.
What does Genuine Presence mean?
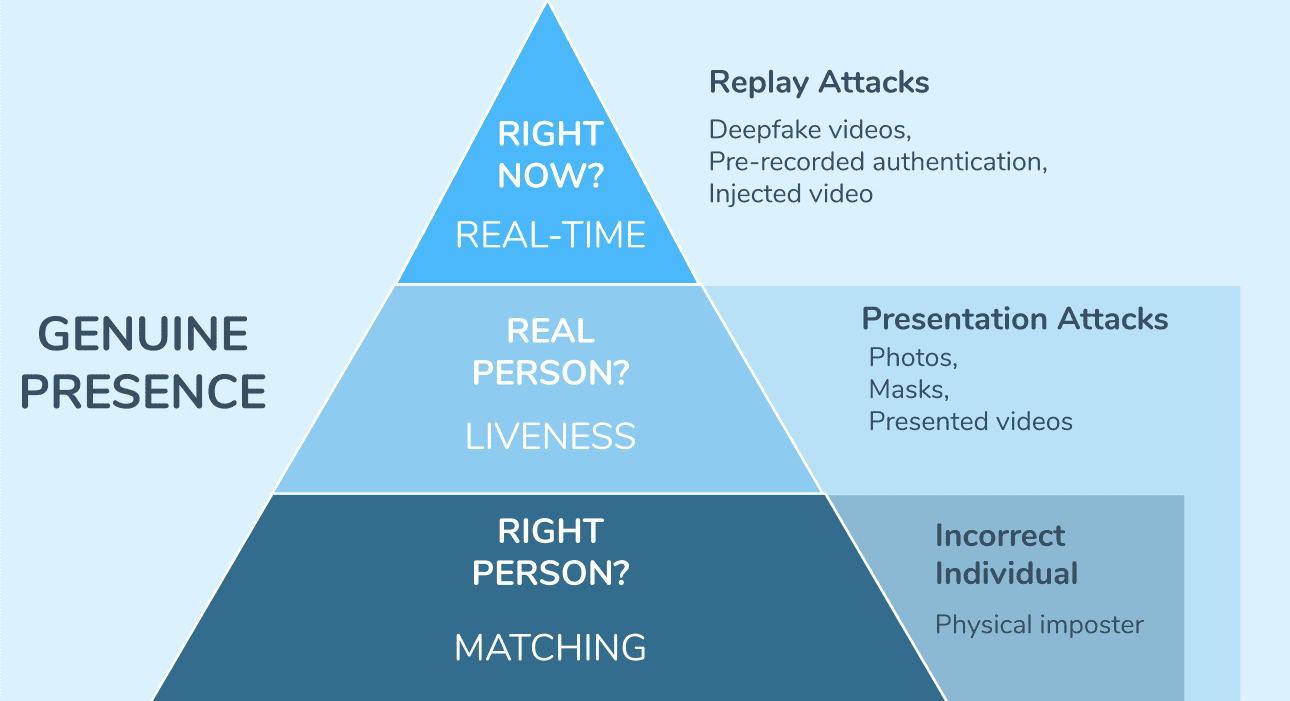
Online Biometric Authentication boils down three tiers of security.
The success of secure biometric authentication is determined by a combination of:
- Matching – is this the right person?
- Liveness – is this a real person?
- Real-Time – is this transaction happening right now?
‘Genuine Presence’ refers to solutions that combine all three tiers. While the majority of the market is still grappling with Liveness – cyber attackers are exploring new, scalable forms of attack that bypass Liveness detection.
So, let’s break down Genuine Presence… tier by tier.
Face Matching: the ‘Right Person’
‘Matching’ is self-explanatory. Matching technology simply matches one set of biometric data to another, to verify the sets of data come from the same person.
Face Matching was first approached in 1964 by a scientist named Bledsoe. His process involved manually entering the coordinates at an average rate of 40 images an hour. We’ve come a long way from there – now matching is a heavily saturated market, with even the most sophisticated face matchers costing as little as 1 cent per match.
Face Matching has been used for surveillance use cases since the late 90s, but more recently Face Matching has been leveraged for Authentication.
Think of setting up a new bank account at home. Instead of going to the branch with your ID in person, with Matching technology you can simply take a picture of your ID and then a selfie. The two images are matched against each other to prove you are in fact the right person.
However, with the increase in face matching for remote, online authentication comes an increase in the exploitation of face matching systems. By now, a lot of people have seen the infamous examples of unlocking the Face Authentication capabilities on smartphones with simply a photo of the device’s owner.
Cue the need for Liveness Detection.
Liveness Detection: the ‘Real Person’
Liveness Detection attempts to verify that we are looking at ‘live user’ by defending against Presentation Attacks. A Presentation Attack is an attempt to pass a fraudulent identity as legitimate, by physically presenting something to a sensor.
In other words, Liveness detection differentiates the real users from the photos, masks and on-screen videos. Liveness detection tells us a user is a Real Person.
There are many methods of doing this – although systems can generally be broken down into two categories:
- Gesture driven (Active systems)
- Technology driven (Passive systems)
Gesture-driven Liveness requires the user to perform a series of unnatural actions to prove that they are real, e.g. blinking or facial movements. Our research shows this approach takes a user on average 2.4 attempts to complete a transaction.
Technology-driven Liveness requires no action from the user, instead using internal algorithms to detect spoofs. This approach takes a user on average 1.1 attempts to complete a transaction.
There was a time when a system differentiating a real face from a highly engineered mask was an impressive feat. However, we have entered a new era of identity spoof attacks. Dangerous cyber attackers don’t spend their time holding photos up to a camera. Presentation Attacks are just a small subset of the attacks that can be launched against a system.
Real-Time Detection: the ‘Right Now’
Real-Time Detection is the next tier of security in online biometric authentication. It is the final step to ensure that you are dealing with a user that is genuinely present, by defending against not only Presentation Attacks, but Replay Attacks.
But what is a replay attack?
Say you perform a successful authentication transaction on your mobile phone. There could easily be malware on your device that you are unaware of. Such malware could record your authentication claim without your knowledge.
A cyberattacker now owns a video of you successfully authenticating. Now, they can bypass the sensor completely (in this case the phone camera) and inject your previous successful claim directly into the app whenever they want.
This form of attack will pass all Liveness defence.
But how?
Because the claim is not of a mask, a photo or a video. The claim is of a real person, really authenticating. However, they are NOT authenticating right now.
Equally as dangerous is the emergence of Deepfake technology. Realistic synthetic videos of your face can be generated from your social media photos – synthetic imagery that Liveness detection is not equipped to deal with. Such synthetic imagery can be generated in real-time and can also be used to bypass the system’s sensors. Deepfakes can be made easily on free-download apps.
These forms of attacks are low-cost and scalable – two qualities that are very appealing to cyber attackers. These attacks are among the most dangerous and the least defended against.
It’s only a matter of time until these attacks are widespread. Will your systems be equipped to identify them?
Genuine Presence Assurance is critical to safeguard digital identity. We won’t stop talking about Genuine Presence until it is the expected standard of security. We also won’t stop innovating. Existing at the cutting edge of authentication – always a step ahead of the latest dynamic threat.